Adaptive Anomaly Control
Attack surface reduction, or hardening, can be a highly effective and inexpensive prevention technique. If you know your system’s vulnerabilities and its excessive functionality, you can proactively block actions that could lead to the exploitation of these flaws.
However, there can be drawbacks in everyday use of such methods. First, general restrictions ignore specific scenarios, which can penalize legitimate users. For example, macros in MS Word documents make it possible to run PowerShell straight from the document, and this ‘useful’ functionality has led to many malware epidemics. But if you block macros activation for the whole company you may find that financial department employees are not happy: they have to use MS Word docs with macros.
Another problem is that manual hardening takes a lot of expert labor. Even for experienced administrators, the adjustment of every blocking rule for a whole lot of different groups and applications would take a prohibitive amount of time. On top of this, new threats and infrastructure changes require that these security policies are regularly revised.
Adaptive Anomaly Control (AAC), a new protection module of Kaspersky Endpoint Security solution, is a smart tool for automated attack surface reduction. This technology enables you to customize system’s hardening right down to the level of the individuals or different groups of users reflecting their various unique requirements while preventing the exploitation of the system’s vulnerabilities or excessive functionality.
Key features of Adaptive Anomaly Control module:
(1) A comprehensive set of effective control rules created by KL experts and based on data retrieved by Machine Learning techniques. Behavior analysis algorithms allow us to find new potential heuristics of suspicious actions in the system, but these actions could be legitimate in some specific instances – so general blocking can’t be used. However, the defining and ‘pinpointing’ of such exceptions by experts can turn these potential heuristics into fully-functioning hardening rules.
A common example of suspicious behavior is when an application is started by some system process: Windows Session Manager, for example, or Local Security Authority Process, or Windows Start-Up Application. There are cases where this could be a legitimate action – for instance, when Windows OS boots up. The experts’ task is to identify these conditions, then create a control rule that would block the execution of applications by the system process– but with appropriate exceptions allowing for the proper operation of OS.
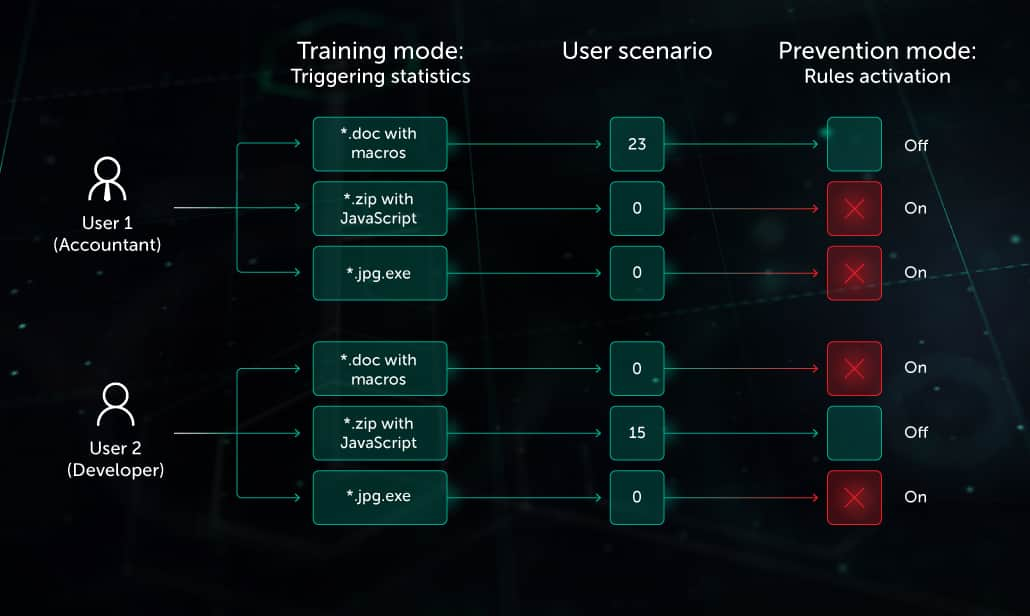
(2) Automated adaptation (Smart Mode) based on user activity analysis. This significantly reduces the need for manual configuration of control rules. First, the AAC module starts to work in Learning Mode, collecting statistical data about control rules triggered over a specific time period - to create a normal activity model for a user or group (legitimate scenario). Then, in Prevention Mode, the system activates only those rules that block the actions anomalous to this group or user’s scenario. If a pattern of normal activity should change for any reason, the AAC module can be switched back to Learning Mode, so it can create a new scenario.
For example, one indicator of a dangerous email attachment is the presence of JavaScript in the archive: Finance Department employees would never need to legitimately exchange such archives. On the other hand, this situation is common among developers. When Adaptive Anomaly Control discovers these different scenarios it will block the attachments with active content for one group of users (Finance Department) but it will not block it for another group (developers).
(3) Fine tuning. Alongside automatic mode, the system admin can control the activation of blocking rules and create individual exceptions, when the behavior to be blocked could be a part of legitimate activity of particular users, applications or devices.
For example, blocking the execution of double extension files (like img18.jpg.exe) would be the correct control rule in 99% of all cases. However, in some systems, double extension files may be used legitimately (update.txt.cmd). In this case, the admin can easily add an exception to allow for this.
(4)Multi-tool synergy. The Adaptive Anomaly Control module not only reduces the attack surface and exposure to threats, including zero-days: it also improves the collaborative performance of Kaspersky Endpoint Security as a part of a Multi-Layered Security platform. The triggering of a particular AAC rule can act as a signal for closer examination of a suspicious object by other protection modules, or by experts.